June 18th 2024 6:41 PM
"I know you'll never get over me. But that's fine. As you said yourself, you won't live that long anymore, so you can at least tell yourself the pain will be over soon."
L.O. (The terrified Victim)
Alerts for July 2025
Update: Escalation, Silence, and Network Moves
1. Mysterious Visitor from Rijeka
A new visitor from Rijeka, just 35km from Krk island, headquarters of the Vogelsang operation, has been methodically checking the site. Sixteen visits on August 19th, followed by periodic returns over two weeks. Instead of landing on the homepage, this person went straight to the ‘Revelations’ and ‘Vogelsang’ pages, lingering for 19 minutes. They also examined pages on ‘Dom and the Narcissist,’ the ‘Segmueller Incident’ (identity theft), and ‘The Job Interview’ (lawsuit by L.O's new employer). This browsing pattern is not random. Whoever it is, they were tipped off, most likely by L.O.'s stepfather, who was the only person I had told about the site.
2. Sudden Silence from L.O.
L.O. has gone completely silent. No phishing, no baiting, no legal threats. The only sign was 11 email openings around midnight on our anniversary, clearly done to provoke a reaction. I'm sure she was disappointed to find out I couldn't care less. But otherwise, nothing. This is not self-restraint (she doesn't have any), it is outside control. Someone in the network has reigned her in, probably because of real legal exposure or the risk of drawing more attention to the criminal network she is apart of. I don't say this lightly, but she and her boyfriend hacked into my accounts in November last year and that makes her a criminal. Something she projected onto me constantly. But she is a thief and a scammer. No doubt about that.
3. Rapid Erasure of Digital Evidence
Suddenly, businesses tied to Octocni Servis are disappearing from Facebook and Google. This is a classic scorched earth maneuver: scrub the web before more evidence gets archived or cross-linked. Car service business, law consultants and tour operators suddenly disappear
4. Flood of Fake Accounts
Within days of discussing fake profiles with J.H., over 150 new “Grabler” accounts appeared on Facebook. This is an obvious attempt to dilute any claims of identity theft or fraud. If there was nothing to hide, there would be no reason for this level of labor-intensive obfuscation. Again, this occurred after I had written to J.H. that I had found fake Facebook accounts in my name as well as his and his stepdaughters name. Remember that this man connected with me on LinkedIn many months prior to my cyberattack that was carried out by his stepdaughter and her alcoholic boyfriend. (They met in a drug rehab clinic in 2019/2020)
5. Clear Coordination
It is now clear: J.H. receives intel and relays it. There is an immediate response from the network. Despite his claims to keep out of L.O.’s affairs, he is at the center of the web. The group is moving as a coordinated unit. Solo actors are gone. I am no longer seen as a threat to one individual. They are protecting the organization.
Conclusion
This is not just a narcissist’s campaign anymore. It is a collective cover-up. Silence from L.O. is enforced, not chosen. The game has changed, but the investigation continues.
July 8th 2025 - 04:15 am
Between 1:00 am and 1:30 am, a fingerprinted user hit this site, scanned ten pages in rapid succession. Device was identified as MacBook Air, Catalina OS, 1400×700 resolution with a VPN through Austria. That signature has been fingerprinted before. It belongs to L.O. It's the same device involved in hacking my accounts in November of 2024.
Less than three hours later, a Quora account using the fake alias Mildred Mildred sent me a single message: "Hello Klaus" No question, statement or anything else. Just two words she hoped would get a reaction.
Hours later my account was suddenly banned. No explanation. My content was deleted and I was history. I have been a member since 2015. The Mildred account was less than 10 days old. No posts. No content, followers, or activity. Yet she knows exactly how to weaponize automated systems meant to protect real users from abuse. She managed to get me banned without a word being said to me or any questions being asked of me.
The ban was reversed 48 hours later after I appealed and the community spoke out. My work on narcissism and abuse is back online, and I will continue to write on the subject. I have written over 260 articles that have garnered around 1.2 million views as of this date.
Below. L.O. impersonating a Quora user in order to bait me into reacting. Who writes a message that simply asks "Hello Klaus"? with no explanation? A few days later my ban was overturned when moderators realized that she had abused the system.
When she 'chose' me, (and she has admitted to me that she did), she did not realize that even though I may be an "Old Fuck" as she calls me, it doesn't mean I will allow her to destroy my life and just walk away to do it again to another victim. She has already cost me my confiscated equipment, my ability to make an income and my naivety.
She’s been trying to silence me for over a year.
I won’t be silenced.
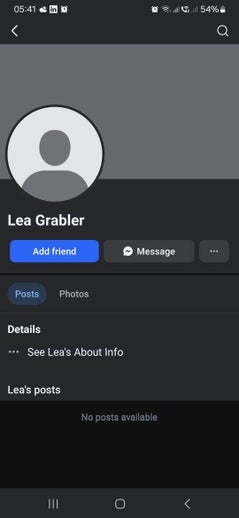
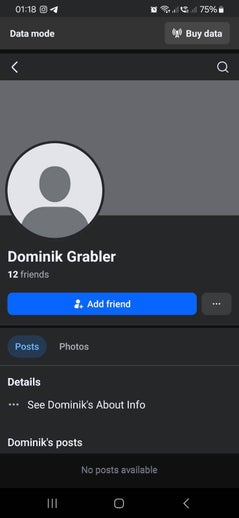
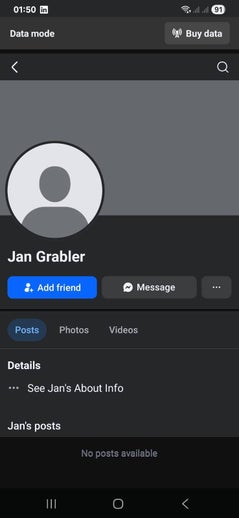
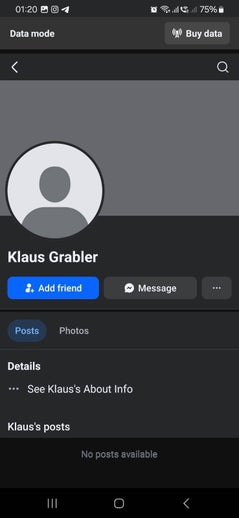
These fake profiles appeared shortly after the cyberattack on me in November 2024. They carry the first names of the people involved but are using my last name. Facebook won't take them down as they are technically not doing anything wrong. Ater reporting this a new swarm of fake profiles appeared all using my surname. Just search for 'Grabler' on Facebook and you'll see them yourself. They are all the blank ones that have no activity.
22nd July 2025 at 03:12am
I’ve been on Facebook for over a decade and have searched for my surname in the past. There were very few Grabler surnames, a handful at most. With fewer than 1,000 Grablers worldwide, new names are rare.
Faced with L.O.’s ongoing attacks, I began monitoring all social platforms. What I found was impossible to miss: two fake accounts, Lea Grabler and a clone of my own profile Klaus Grabler empty, ready and waiting. Dominik Grabler. Then came Jan Grabler.
Nothing for a while after that. I did receive notices that someone was buying luxury furniture and vehicles in Germany using my email address and my name.
Today it escalated. I uncovered over 150 new fake “Grabler” accounts on Facebook. No photos. No posts. No friends. Empty shells. This is no coincidence.
Here are the confirmed fakes so far:
Marius Grabler, Sabine Grabler, Christian Grabler, Sophia Grabler, Hans Martin Grabler, Belane Grabler, Katharina Grabler, Lisa Grabler, Finja Grabler, Marc Grabler, Andre Grabler, Werner Grabler, Andre Grabler, Alon Grabler, Simon Grabler, Lea Grabler, Stefan Grabler, Kilian Grabler, Franz Grabler, Silvia Grabler, Martina Grabler, Andre Grabler, Henry Grabler, Mathias Grabler, Klaus Grabler, Valentin Grabler, Andre Grabler, Myrtle Grabler, Slavko Grabler, Magdalena Grabler, Theresa Grabler, Katrin Grabler, Richard Grabler, Michael Grabler, Ciccarone Grabler, Stefan Grabler, Katrin Grabler, Mary Grabler, Max Grabler, Gary Grabler, Maja Grabler, Ciccarone Grabler, Florian Grabler, Imke Grabler, Ulrike Grabler, Markus Grabler, Karl Grabler, Elke Grabler, Jan Grabler, Günther Grabler, Mathias Grabler, Linda Grabler, Silvia Grabler, Florian Grabler, Alon Grabler, Maria Grabler, Hannah Grabler, Kate Grabler, Fortnite Grabler, Monder Grabler, Claudia Nickie Grabler, Marilia Grabler, Dominik Grabler, Sal Grabler, Samantha Grabler, Jacqueline Grabler, Grabler Marc, Imke Grabler, Christian Grabler, Brian Grabler, Brian Grabler, Ava Grabler, Roswitha Grabler, Jaime Grabler, Kevyn Grabler, Kylie Grabler, Anton Grabler, Dusan Grabler, Daniela Grabler, Kilian Grabler, Valladar Grabler, Grabler Matthias, Marc Grabler, Pamela Grabler, Leona Grabler, Lina Grabler, Alex Grabler, Devereux Grabler, Dušan Grabler, Reannon Grabler, Roberta Grabler, Anton Grabler, Dylan Grabler, Baki Grabler, Sebastian Grabler, Crawford Grabler, Kae Grabler, Anne Grabler, Damien Grabler, Stewart Grabler, Lizzy Grabler, Jillian Grabler, Flora Grabler, Deshawn Grabler, Providencia Grabler, Raffael Grabler, Malakai Grabler, Sven-Åke Grabler, Gabrielle Grabler, Alise Grabler, Jon Grabler, Rene Grabler, Mette Grabler, Lowell Grabler, Steven Grabler, Kamala Grabler, Hermine Grabler, Andrea Grabler, Thomas Gräbler, Margart Grabler, Godfrey Grabler, Geffrey Grabler, Michael Grabler, Jackie Grabler, Jean-claude Grabler, Caedmon Grabler, Lavina Grabler, Braidy Grabler, Amer Grabler, Jimmie Grabler, Claudius Grabler, Valerie Grabler, Christopher Grabler, See Grabler, Olivia Grabler, Hannes Grabler, Michael Grabler, Hepsie Grabler, Lena Grabler, Linda Grabler, Brandon Grabler, Martin Grabler, Exie Grabler, Dacia Grabler, Sebastian Grabler, Kilian Grabler, Michael Grabler, Franc Grabler, Herbert Grabler, Slavko Grabler, Mark Grabler, Stefan Grabler, Luba GrablerFranc Grabler, Susanne Grabler, Franc Grabler, Teran Grabler, Michael Grabler, Maria Grabler, Sarah Grabler, Magdalena Grabler, Franc Grabler, Nico Grabler, Mariam Grabler, Zoe Grabler, Chucky Grabler, Maike Grabler, Steffi Grabler, Raisa Grabler.Marius Grabler, Sabine Grabler, Christian Grabler, Sophia Grabler, Hans Martin Grabler, Belane Grabler, Katharina Grabler, Lisa Grabler, Finja Grabler, Marc Grabler, Andre Grabler, Werner Grabler, Andre Grabler, Alon Grabler, Simon Grabler, Lea Grabler, Stefan Grabler, Kilian Grabler, Franz Grabler, Silvia Grabler, Martina Grabler, Andre Grabler, Henry Grabler, Mathias Grabler, Klaus Grabler, Valentin Grabler, Andre Grabler, Myrtle Grabler, Slavko Grabler, Magdalena Grabler, Theresa Grabler, Katrin Grabler, Richard Grabler, Michael Grabler, Ciccarone Grabler, Stefan Grabler, Katrin Grabler, Mary Grabler, Max Grabler, Gary Grabler, Maja Grabler, Ciccarone Grabler, Florian Grabler, Imke Grabler, Ulrike Grabler, Markus Grabler, Karl Grabler, Elke Grabler, Jan Grabler, Günther Grabler, Mathias Grabler, Linda Grabler, Silvia Grabler, Florian Grabler, Alon Grabler, Maria Grabler, Hannah Grabler, Kate Grabler, Fortnite Grabler, Monder Grabler, Claudia Nickie Grabler, Marilia Grabler, Dominik Grabler, Sal Grabler, Samantha Grabler, Jacqueline Grabler, Grabler Marc, Imke Grabler, Christian Grabler, Brian Grabler, Brian Grabler, Ava Grabler, Roswitha Grabler, Jaime Grabler, Kevyn Grabler, Kylie Grabler, Anton Grabler, Dusan Grabler, Daniela Grabler, Kilian Grabler, Valladar Grabler, Grabler Matthias, Marc Grabler, Pamela Grabler, Leona Grabler, Lina Grabler, Alex Grabler, Devereux Grabler, Dušan Grabler, Reannon Grabler, Roberta Grabler, Anton Grabler, Dylan Grabler, Baki Grabler, Sebastian Grabler, Crawford Grabler, Kae Grabler, Anne Grabler, Damien Grabler, Stewart Grabler, Lizzy Grabler, Jillian Grabler, Flora Grabler, Deshawn Grabler, Providencia Grabler, Raffael Grabler, Malakai Grabler, Sven-Åke Grabler, Gabrielle Grabler, Alise Grabler, Jon Grabler, Rene Grabler, Mette Grabler, Lowell Grabler, Steven Grabler, Kamala Grabler, Hermine Grabler, Andrea Grabler, Fortnite Grabler? Really?
Fake Facebook profiles are typically created in bulk using automation tools and scripts that mimic real users. The process begins with selecting a real surname, like Grabler, and combining it with random first names to generate dozens or even hundreds of seemingly legitimate identities. These fake profiles are registered using automated browsers or bots, often running through VPNs to mask their origin and bypass Facebook’s security checks. CAPTCHA-solving services are sometimes used to trick the platform into thinking a real person is signing up.
Once created, the profiles are left mostly empty, no photos, no posts, and usually just one or two friend connections, often with other fake accounts. The goal is not to build active social lives, but to flood the network with decoys that confuse search results, enable impersonation, or create the illusion of a larger presence around a name. In more malicious cases, this tactic is used to bury or isolate the real person by surrounding them with fake digital shadows.
A known fingerprinted device, MacBook Air, Catalina OS, accessed the newly updated Vogelsang page three times recently from Germany. L.O. is nervous. I have also seen that communication from Dom on Telegram seems to have halted. Could be due to him creating a new account or because she returned him to his shelf as she is busy with a new victim.
Car Finance using my name
Additional evidence of identity theft arrived that seems to show Car finance fraud being committed. This is in addition to the already documented Segmüller Furniture company fraud.
Further sign of fraud and identity theft. A partially completed car finance request. My name is apparently being used to purchase vehicles.
The company refuses to address my concerns or to even answer me anymore.
Below:
Reply from the German Police in regards to pressing charges. I have since filed a list of cybercrime charges against L.O. Authorities arrived a week after I laid the charges to collect all of my evidence against her.
German Hotel California
Below: A hotel where you can never book a room, a Lisa Vogelsang property sold to a wealthy Sheik that is still pretending to be a functioning hotel, in the center another attempt by L.O. to try and get a reaction from me , this time on Xing, and evidence how I was blocked the moment I told L.O.'s stepfather I had contacted the Vogelsang Detektei WhatsApp group. The Your Pilots.de later changed their business from tour operator to property developer. They are all fake businesses.
Cybercrimes and Digital Harassment Campaign
Overview
This summary documents a sustained, sophisticated cybercriminal campaign involving identity theft, digital surveillance, platform manipulation, and coordinated harassment across multiple countries from November 2024 through at least January 2025.
Key Perpetrators Identified
- L.O.- Initial Contact/Long Distance Romance Scammer/ Abuser/ Covert Narcissist/ NPD sufferer/ Rastatt, Germany
- Dom - Hacker, Northern Germany
- Lisa Vogelsang - Infrastructure provider (shell companies, private investigation services) Location Unknown
- J.H. - Coordinator/intermediary/ Stuttgart, Germany
Documented Criminal Activities
1. Identity Theft & Financial Fraud
-
German Furniture Purchase - Fraudulent order established fake German residence
-
Vehicle Finance Fraud - Santander Bank car loan approved in victim's name (July 8, 2025)
-
Multiple Fake Social Media Profiles - "Lea Grabler," "Klaus Grabler," "Jan Grabler" Facebook accounts
2. Account Compromises (November 2024)
-
20+ accounts breached including email, social media, financial services
-
Cryptocurrency theft attempted
-
Unmasked IP captured: Hemmoor, Germany (Location confirmed)
3. Sophisticated Digital Surveillance
Constant monitoring and stalking by fingerprinted devices linked to L.O.
4. Platform Manipulation & Censorship
- Quora Account Destruction (July 2025)
- 10-year-old account banned
- 260 articles on narcissistic abuse deleted
- 1.100,000 views erased
- Used by "Mildred Mildred" account (created 10 days prior, followed only victim)
5. Direct Cyber Attacks
- Malware Attack (July 7, 2025)
- Spoofed Gmail bounce-back messages
- AWS S3 hosted malware payload
- Attempted credential theft and system compromise
- Phishing Campaign (July 7, 2025)
- Sophisticated Webador payment scam
- Hidden Wondershare code injection
- Multiple tracking pixels
Technical Capabilities Demonstrated
- Enterprise-grade surveillance tools
- Browser fingerprint manipulation
- Multi-layer VPN/proxy chains
- Infrastructure abuse (Google, Meta datacenters)
- Coordinated multi-platform attacks
- Professional malware deployment
- International money laundering structures
International Scope
- Germany: Primary operations base, identity theft
- Croatia: Shell company network
- Multiple VPN endpoints: Netherlands, Austria, etc.
Current Threat Assessment
- Active, ongoing campaign with daily surveillance
- Escalating tactics from monitoring to direct attacks
- Significant resources indicating professional criminal operation
This represents a sophisticated case of narcissistic abuse weaponized through professional cybercrime capabilities.
Above: My investigation Mind map. From a Drug rehab attended by L.O. and Dom to the namesake Detective agency that has ties to several fake businesses as well as her stepfather, this is a complicated web to untangle.
Summary of Evidence.
Following our implementation of IP blocking for Meta/Facebook infrastructure on July 4th, the monitoring users changed tactics and returned again hoping they would be able to go undetected.
Primary targets of interest:
Our Security Documentation - They accessed our security logs page twice, clearly trying to understand what we know about their operations and how we're tracking them. This shows they're concerned about our evidence collection capabilities.
J.H.'s Story - Significant time spent reading about the stepfather's involvement, suggesting this area represents a vulnerability or concern for their operation. They may be worried about what J.H. has revealed or might reveal.
Legal Analysis - Deep focus on false charges documentation, indicating they're trying to understand our legal position.
Criminal and Psychological Profiles - They studied our NPD analysis, possibly to understand how we've profiled their behavior patterns or to gauge our psychological insights into their operations.
Professional Infrastructure: The operatives used premium VPN services from Sabotage LLC in the Netherlands and Foundation for Applied Privacy in Austria. These are not cheap consumer VPN services but professional-grade privacy tools used by serious threat actors.
Advanced Location Obfuscation: They configured their system to show an origin timezone of Atlantic/Reykjavik (Iceland), which doesn't match their actual VPN endpoints in Amsterdam and Vienna. This level of timezone spoofing indicates sophisticated operational security awareness.
Browser Configuration: Firefox 128.0 in incognito mode with enhanced privacy settings enabled, showing they understand digital forensics and are trying to minimize their fingerprint.
Multiple Exit Points: They used two different VPN servers during the session, switching from Netherlands to Austria infrastructure, demonstrating professional tradecraft.
The systematic, methodical nature of this intelligence gathering suggests this wasn't a low-level operative but someone with decision-making authority who needed to personally assess the threat level. The focus on legal strategy and security methods indicates they're not just monitoring but actively planning responses to our investigation.
Enhanced Monitoring: We've implemented additional tracking for premium VPN services and privacy networks commonly used by sophisticated threat actors. The fact they're studying our evidence suggests our documentation is having the intended effect of creating accountability pressure and legal exposure concerns. After the recent malware attacks we continue to maintain secure backup systems and evidence preservation protocols, anticipating potential escalation or counter-attacks. Their focus on our legal documentation confirms the importance of maintaining comprehensive evidence files for potential criminal proceedings.
Assessment
This intelligence and observation operation represents a significant development in the ongoing harassment campaign. The shift from automated surveillance to human intelligence operations indicates our investigation has reached a critical point where the intruders feel compelled to invest serious resources in understanding and potentially countering our evidence collection.
Alerts for August 2025
August 2025
Forensic User Report – Rijeka (Suspect this could be J.F., associate of L. Vogelsang)
Date: August 19, 2025
IP: 93.138.141.140
Device: Windows 11 (Opera 120, Chrome 135 engine)
Screen Resolutions Noted: 384x659, 384x755
Summary of Activity
-
Session Start: /investigations/vogelsang/urlaub-krk at 20:15 (local time)
-
Total Pages Visited: 18+
-
Browsing Duration: Appears to be a rapid session, with less than 2 minutes per page in most cases.
-
Key Sections Viewed:
-
Investigations: Vogelsang (including Urlaub-KRK), Turning Point, Part One/Two
-
Forensic Reports: Vogelsang network
-
Revelations: Realization, Silent Conspiracy, Dom and the Narcissist, The Job Interview
-
My Story: Introduction, Phase 1, My Story main
-
Threads: The Documentary
-
Psychology: The Psychology
-
Behavioral Analysis
-
High-Focus Navigation:
The visitor is not casually browsing; instead, they are methodically working through high-value, sensitive sections (investigations, forensic reports, personal narrative). The page sequence and speed suggest a specific agenda or checklist. -
Motivation Inferred:
-
Fact-Checking/Monitoring: The user appears to be fact-checking or scanning for references to themselves or their network (the Vogelsang case is repeatedly accessed).
-
Damage Assessment: The sections viewed are those that would detail new evidence, expose hidden facts, or reveal new names, typical of someone monitoring reputational risk.
-
Pattern of Control: Fast transitions indicate a user looking to quickly “audit” the narrative, possibly to preempt or plan countermeasures.
-
-
Technical Clues:
-
Consistent IP/Location: No attempt to hide location (Rijeka, Croatia).
-
Resolution Changes: Window resized during session, likely due to copying or screenshotting content, or switching device orientation.
-
-
Psychological Profile:
This is a defensive, possibly anxious behavior pattern. J.F. is almost certainly checking for updates on what I know, what I’ve published, and how it connects to her or her associates. The session is not that of a casual observer, it’s a surgical sweep.
Conclusion
-
Motivation: Monitoring for new incriminating material, references to self, or the Vogelsang network.
-
Method: Fast, targeted navigation, not a deep reader, more an auditor.
-
Action: Profile further.
-
Advisory: This user is on the site to stay ahead of the revelations, not to learn.
LATEST INCIDENTS:
22nd August 2025
Incident Report: Unauthorized WhatsApp Verification Codes
Date: 22 August 2025
Summary:
On 22 August 2025, I received two unsolicited WhatsApp verification codes via SMS. I did not request these codes, nor did I attempt to register a new device. This indicates that a third party attempted to access or register WhatsApp using my phone number. No account access was granted, and two-step verification remains active. The incident has been documented as a potential account takeover attempt.
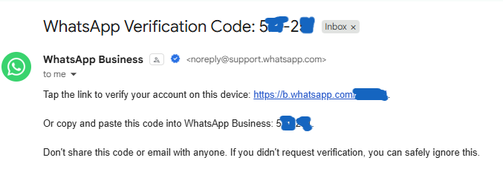
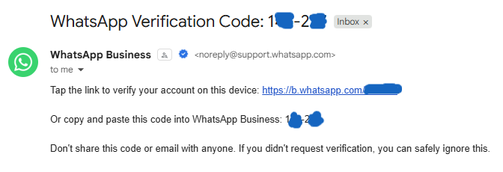
Visitor Logs
August 2025
Forensic Log Entry – Suspicious Visitor
Date/Time: 23 August 2025, 17:01–17:09 UTC
IP Address: 51.159.225.150 (Scaleway/Online SAS, Haarlem, Netherlands)
Visitor ID: Rplfao5qfz800CvN4wsM
Device: Chrome 139 / Linux, running in Virtual Machine
VPN/Privacy: Yes (timezone mismatch: set to Moscow, exit node Netherlands), high OPSEC
Bot Detected: No (human-like browsing; no crawler signature)
Incognito/Proxy: No / No
Pages Accessed:
-
Landed on: /my-story/introduction (spent 7 minutes)
-
Rapidly browsed 4 additional pages in under 1 minute
Summary of Activity
At 17:01 UTC, a visitor entered the site from a Scaleway/Online SAS datacenter IP in Haarlem, NL, presenting as a Chrome 139 browser running on Linux within a virtual machine. The connection was routed through a VPN (with their internal timezone set to Moscow, further distancing their true location).
Upon landing, the visitor remained on the introduction page for seven full minutes—far longer than a typical visitor. This dwell time suggests either a careful, detailed review or the use of recon tools/scripts to analyze the site’s entry point and page structure. No obvious signs of automation or botting were detected.
After this extended pause, the user clicked through four more site pages in rapid succession—spending less than a minute total on all of them. This rapid-fire navigation is consistent with a targeted mapping attempt rather than genuine interest in site content.
Key Observations
-
Advanced Anonymity: Use of both a datacenter-based VPN and a virtual machine, plus timezone obfuscation, signals a visitor highly concerned with privacy and attribution.
-
Reconnaissance Pattern: The long landing-page pause followed by quick, systematic page hits is classic reconnaissance or site mapping behavior, not typical user browsing.
-
No Prior History: The visitor ID was first seen on this date; this was not a returning, fingerprinted user.
-
No Bot/Crawler Activity: Human-like interaction; not a search engine or standard data-mining tool.
Assessment
This is not a routine user or accidental visitor. The use of technical privacy layers, VM isolation, and deliberate browsing cadence points to that.
Level of Concern: Elevated. The session suggests deliberate surveillance, technical proficiency, and a direct interest in your narrative or evidence. Not a random visitor.
Conclusion:
Whoever this was, they went to great lengths to avoid leaving a trace
Ströer Erases Authorship from Blog. Proof of a Coordinated Digital Cover-Up
25 August 2025
Today, I confirmed that all articles previously featuring L.O.’s byline have been scrubbed from the Wayback Machine archives. While the articles themselves remain online at the Ströer Online Marketing blog, every author byline has been systematically removed, in fact no articles on the site now display any author at all.
This move is not isolated to L.O.’s work; it represents a full-scale revision of the site’s content attribution, conveniently erasing the digital paper trail linking L.O. to her original published work. Not one of the other authors can now claim authorship as there are no more bylines. Notably, her authorship had previously been altered (in one case, replaced with the name Alexander Graf), and now, even third-party archives show meddling and redacted metadata, strongly suggesting a coordinated effort between L.O. and Ströer during their vociferous denials that anything underhanded was going on.
Conclusion:
This is direct evidence of a calculated, large-scale attempt to rewrite L.O.'s digital history and obscure the true origins of the content, an effort that spans both the live website and external archives.
I wonder what influence she has that she can so easily get entire companies to bend to her will, despite the fact that they are aware that she has forged they very own documents in order to obtain alternate employment. I have supplied them with evidence of this forgery, yet they choose to assist her in deleting all evidence of her existence.
The fact that dozens of innocent up and coming authors now have no more portfolio of published articles to point to as all the bylines have been removed to protect one woman who is pretending to be the victim when she is in fact the abuser will not concern her in the least.
Weekly Security Summary: Surviving the Storm
Reporting Period: up to August 25th
-
Unique Visitors: 129
-
Average Events per Visitor: 3.13
-
API Calls: 404 (no throttling detected)
-
Total API Calls This Billing Period: 485
Smart Signals Breakdown:
-
Virtual Machines Detected: 14 (4.56%)
-
Incognito Visits: 18 (5.86%)
-
VPN Usage: 28 (9.12%)
-
Tampering Attempts: 4 (1.3%)
-
High Activity Sessions: 31 (10.1%)
-
Bad Bots Identified: 3 (0.98%)
-
Good Bots Identified: 2 (0.65%)
Observations:
-
Elevated VPN and Incognito usage indicates continued attempts to evade tracking.
-
High activity and VM rates suggest automated surveillance or scripted scraping.
-
No API throttling or denial events, system functioning within normal parameters.
No immediate action required, but continued monitoring advised.








