"And one last thing. You were absolutely right with your arse-kissing emails . You've always been jealous of me. You couldn't stand the fact that my "childish" videos got more views than yours. And even now you realize that I outdo you argumentatively, that I always outdo you, even though I'm 30 years younger than you. That's why contact with you bores me by now. You said it yourself, I am called to something better than you." L.O. Narcissist (The terrified Victim)
Desperate Descent
Reactive Abuse
In the days after the discard, I became more and more distraught. Not because I needed closure, I'd long stopped expecting honesty from her, but because I couldn’t believe she would actually go through with it. She had pulled similar stunts before. Silent treatments, then withdrawals. But she had always returned. Always. But it was different this time. I could feel it. Something had changed, and I got the feeling that I had missed something. But I couldn't think straight. I was getting desperate. The addiction of the trauma bonding was kicking in. I was suffering withdrawals.
Zero Reaction
So I didn’t seek understanding. I sought reaction. I wanted her to respond, to prove I still mattered. I wanted her to acknowledge my existence. I bombarded her inbox, dozens of emails per day, and I poured out my rage and confusion in messages she never answered. My words shifted from pleading to threatening to insulting. Anything to elicit a response, an acknowledgement. Not because I hated her, but because I couldn’t bear the sudden vacuum. The ghosting wasn’t just silence. It was annihilation. How could she do this, I wondered. She could do it because she truly never cared. And because she knew I had been abandoned as a child.
And that, I now see, was the design. She wanted me to spiral out of control. She wanted the paper trail. A collection of emails that, stripped of context, made me look unstable, obsessive, unhinged. She didn’t just discard me. She laid the groundwork for a future accusation, knowing exactly how I would react. This was not the first time she had done this. She expected me to react badly and she made sure there would be evidence of it. This was the aim all along. Get me to react badly and keep the "evidence" for further down the road.
The Perfect Victim
I was desperate. My feelings for her had been real, so when the realization hit home that I had been played by someone who did not care one bit, I lost it. I wrote emails threatening her, verbally abusing her, begging, pleading, I tried everything to get a reaction. It was the psychological snap of someone whose trust had been exploited, whose hope had been used against him, and whose love had been weaponized for narrative control. You can only take so much before you snap. Everyone has their limit. Narcissists know exactly how to push you towards it. It's why they study you so hard in the beginning.
Psychologists call it reactive abuse, when the victim finally lashes out, unable to take the abuse any longer, and the narcissist calmly steps into the role of the wounded party. Suddenly the abuser takes the role the victim and the victim becomes cast as the abuser. Complete with "Evidence". It’s a setup. And I walked right into it.
This was the start of the war. A silent war, provoked with precision, and one I never saw coming.
A Narcissists Revenge
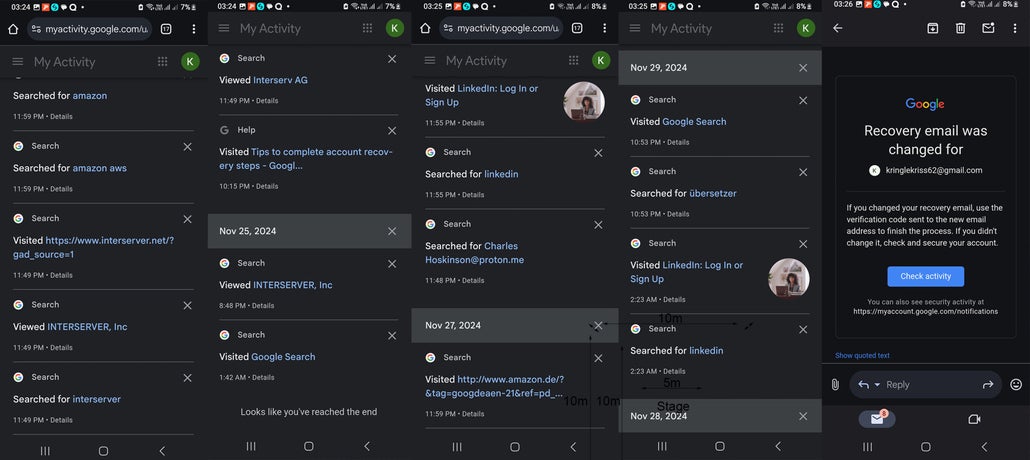
Below: This composite screenshot captures unauthorized activity on my kringlekriss69@gmail.com Google account between 25 November 2024 and 29 November 2024, during a confirmed four-day breach. L.O. and Dom used the account to conduct targeted searches, including recovery protocols, hosting platforms (InterServer), and email accounts (e.g. charleshoskinson@proton.me). The final frame confirms that the recovery email on kringlekriss69@gmail.com had been changed, proving the account had been hijacked.
Above: This image serves as clear evidence of the hack, the premeditated stalking behavior, and the psychological warfare tactics used during that time. I was able to recover the account weeks later and discovered these activity logs they had evidentially forgotten to delete.
I also found evidence of L.O. trying to frame me by subscribing to XHamster using her real name with this email address. She later tried to delete the account but I managed to recover it for evidence. This fact alone proves that she was involved in the hacking of this account and therefore all the associated ones too.
November 28 – December 1, 2024:
The Attack Unfolds – A Detailed Chronology
November 28, 2024:
The intrusion began. A Google confirmation code landed in my inbox, a red flag for an attempted account recovery and likely email reset. Within hours, my digital world was under siege:
-
Blofin: Nine separate verification code requests, signs of repeated forced-entry attempts.
-
LinkedIn: PIN sent to my “Kurt” account (977895), followed by a password reset confirmation and a verification code with no identifying name.
-
XT.COM: Password reset verification.
-
Email: I sent two messages to my own compromised ProtonMail in an attempt to communicate with the hackers. No reply was received. Clearly ransom was not the motive.
November 29, 2024:
The pace intensified:
-
Otoy Account: A password restoration attempt flagged a new front in the attack.
-
Substack: A series of notifications, from password setup to login attempts, appeared in rapid succession.
-
Bybit: Security codes were requested twice, followed by a password change confirmation and login alert. Oddly, the account’s email address remained unchanged, suggesting disruption rather than theft.
-
OKX: A password change attempt.
-
Altcointrader: Within ten minutes, my account was logged into, the password was changed twice, then login approvals and a successful login followed.
-
BingX: Multiple attempts to modify verification options.
-
XT.COM: Another login alert and a phone reset attempt.
-
ProtonMail: Verification code received with an attachment, likely a phishing attempt.
-
LinkedIn: Notification of a profile name change and more device registrations.
November 30, 2024:
Damage escalated:
-
Altcointrader: Account disabled notification arrived at 00:21.
-
LinkedIn: Three new device registrations for “Remember me,” followed by an account deletion confirmation that read “We’re sorry to see you go.” This was the Kurt Wagner account she had used to send me the message.
-
ProtonMail: I sent several urgent messages to my own compromised account, None were answered.
December 1, 2024:
The silence from the attackers continued:
-
Another email from me. No reply.
-
Blofin Support: Two confirmations of email change attempts.
-
Badoo: Verification code issued. Another sign up to a disreputable website.
-
Deepcoin: Password change confirmation.
-
OTOY: Octane Render subscription cancelled.
-
XT.COM: Three new security notices.
Attack Analysis
The pattern here is no accident. It reveals:
-
Systematic progression: The assault started with email, spread to financial platforms, moved to professional accounts, and ended with personal harassment.
-
Escalating sophistication: Early moves focused on account access, but later actions aimed at identity manipulation and psychological pressure.
-
Targeted knowledge: The hackers hit rarely-used accounts and niche tools, which is clear evidence of prior surveillance.
-
Disruption, not just theft: Access to crypto exchanges was achieved, but the attackers’ focus was more on chaos and intimidation than on draining funds.
-
No response to engagement: Despite my attempts to open a channel, the hackers never replied. Some of my messages were left unread, showing their goal was destruction, not negotiation.
-
Evidence manipulation: Accounts were accessed, altered, then in some cases deleted. This points to efforts not just to steal or harass, but to falsify digital evidence and cover their tracks.
Why This Matters
This was not a random hack. The careful sequencing, rapid execution, and surgical targeting show a campaign built on inside knowledge, likely orchestrated by someone with an intimate grasp of my online life as well as access to my account and login details. Only attainable through use of spyware and keyloggers.
It is evidence not just of cybercrime, but of a coordinated psychological attack, blending technical expertise with personal malice.
Prepared to Wait
November 27th 2024: 2:23 AM - 22:12 PM
While illegally logged into my kringlekriss62@gmail.com account, they accessed LinkedIn, logged into a secondary account only L.O. knew existed, and waited nearly 20 hours for me to login to my regular account before sending a taunting message. It read: “i hope u’r well. for now… have a nice time!”
This was no random hacker. It was a signature. Her signature. The lowercase letters and clipped phrasing were deliberate, meant to show me how little I was worth. After nearly three months of silence, this was her way of showing that she still held control. And that I meant nothing. This was her narcissistic revenge, detached, cruel, and unmistakably personal. I found the level of hate she was showing hard to believe.
I realized later she had sworn revenge for the narcissistic injury I had caused her when she was banned from the PIKA platform. Her 'love' had turned to hate, and her need for revenge was all consuming. This is what the psychologists term "narcissistic rage".
The message sent by L.O. to my LinkedIn account
On the right are screenshots of the Apple Mac that was logging onto my Gmail account each day. For four days she caused havoc with my email account. L.O. uses a Apple Mac computer.
Below: Evidence - a screenshot from my investigation into this incident. As can be seen by the date it is clear she was in the habit of "calling the whole thing off", only to later reappear and hoover me back again, typical of narcissistic abuse cycles. Note the use of aliased emails. The style of writing is similar to her previous known emails and is corroborating evidence.
Below: Here you can see her by own admission that she knew my email login details. This email was another attempt by her to blackmail me. One of many such attempts.

The hacking that happened in November of 2024 was well planned, coordinated and carried out with the intent to cause maximum damage. The Cyber Attack was swift and well planned. She showed me now that she was intent on destroying me. I still do not understand why.